Mapping the SANS 20 to NIST 800-53 to ISO 27002

The SANS 20 Overview
SANS has created the “20 Critical Security Controls” as a way of providing effective cyber defense against current and likely future Internet based attacks. Following these 20 controls will help establish, in their words, a “prioritized baseline of information security measures and controls.” The target audience is Federal enterprise environments but it certainly could be used by commercial organizations. Let’s take a quick look at the specifics of what the control areas are and how they are organized.
Control Area Organization
Each of the 20 critical areas is organized using the same subsections:
- How do attackers exploit the lack of this control?
- How can this control be implemented, automated, & its effectiveness measured?
- Associated NIST SP 800-53 Priority 1 Controls
- Procedures & tools for implementing & automating this control
- Control metric (what the control should deal with)
- Control test (how to evaluate the control)
Critical Security Controls
The 20 Critical Controls are broken into two categories: the first sets of 15 controls lend themselves to automation.
Critical Controls Subject to Automated Collection, Measurement, and Validation:
- Inventory of Authorized & Unauthorized Devices
- Inventory of Authorized & Unauthorized Software
- Secure Configurations for Hardware & Software on Laptops, Workstations, & Servers
- Secure Configurations for Network Devices such as Firewalls, Routers, & Switches
- Boundary Defense
- Maintenance, Monitoring, & Analysis of Audit Logs Application Software Security
- Controlled Use of Administrative Privileges
- Controlled Access Based on Need to Know
- Continuous Vulnerability Assessment & Remediation
- Account Monitoring & Control
- Malware Defenses
- Limitation & Control of Network Ports, Protocols, & Services
- Wireless Device Control
- Data Loss Prevention Additional Critical Controls
- Secure Network Engineering
- Penetration Tests & Red Team Exercises
- Incident Response Capability
- Data Recovery Capability
- Security Skills Assessment & Appropriate Training to Fill Gaps
Is This a New Standard?
No, the SANS 20 Critical Security Controls is not a new standard. This is a set of recommendations developed by a consortium of companies with the purpose of identifying specific controls that will make systems safer. In addition, most of the controls can be automated (to various degrees) through the use of tools.
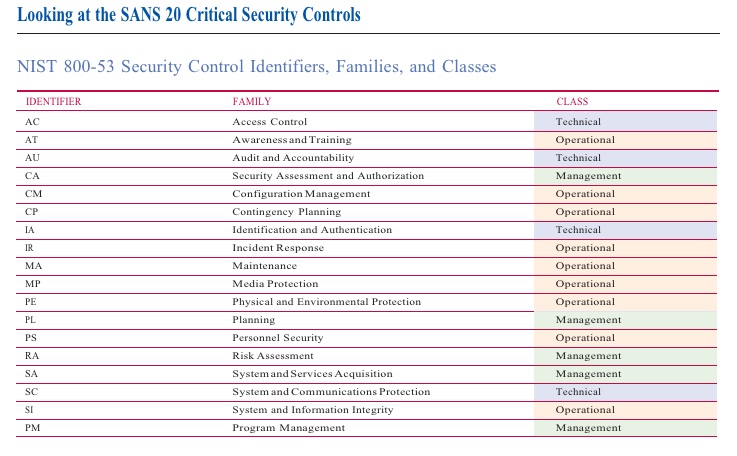
There is a direct mapping between the 20 controls areas and the NIST standard “Recommended Security Controls for Federal Information Systems and Organizations” which is referred to as NIST Special Publication (SP) 800-53. The SANS 20 Critical Security Controls represent a subset of the NIST SP 800-53 controls (in fact, it covers about one third of the 145 controls identified in NIST 800-53).
From SANS’s point of view, focusing on these 20 areas will help an organization be prepared for the most important actual threats that exist in today’s Internet world. In addition, the first 15 control areas lend themselves to tool based assessments so an organization has a chance to fulfill most of them in an automated or semi-automated way. Most of the control areas are focused on technical controls and not so much on operational or management oriented NIST controls. Therefore, SANS believes that following their 20 Critical Security Controls will directly help protect your systems against current threats and cyber attacks.
Mapping the SANS 20 to ISO 27002
If you are not a government agency, however, you probably are not using the NIST SP 800-53 security standard as a framework for auditing your IT environment. Many private organizations instead use the ISO 27001/27002 information security standards.
From my point of view, focusing on control areas that provide practical and tangible progress for preventing or detecting actual threats is a good idea. To help understand how these control areas map to a standard that you are probably more familiar with or are already using to evaluate your own environment, I have created a table that shows how the SANS 20 Critical Security Controls maps to the NIST 800-53 standard and then how those controls map to the ISO 27002 standard.
Understanding the big picture
SANS has done a good job of trying to distill a complex problem (protecting your networked resources from cyber attacks) into a series of straightforward security controls. There are other things you should consider if you are going to use the 20 Critical Security Controls as a benchmark.
In all likelihood, management and operational controls, policies, and procedures are going to provide the security umbrella you need to protect corporate assets and information. Tools are helpful for automating tasks, but tools and technologies are only as useful as the management and operational infrastructure that is using them. Being prepared for serious problems such as Advanced Persistent Threats are not going to be solved by technology alone.
SANS has identified a set of tools that have been “vetted” by users to help automate some of the Security Control areas. This list is largely based on input from users who have been involved in helping to create the SANS 20 recommendation. There are other third-party and public domain tools that are similar to the ones listed or may be more appropriate for you to use.





SANS Control Poster:




I know this if off topic but I’m looking into starting my own weblog and was curious what all is needed to get setup? I’m assuming having a blog like yours would cost a pretty penny? I’m not very internet smart so I’m not 100 sure. Any tips or advice would be greatly appreciated. Many thanks
LikeLike
Dear Trudy,
a website like mine on WordPress is completely for free if you are using the basic version.
However if you would use the version with a plan you can also create your own domain name and many other extra’s.
Good luck and wishing you well Trudy
LikeLike
Dear Trudy,
a website like mine on WordPress is completely for free if you are using the basic version.
However if you would use the version with a plan you can also create your own domain name and many other extra’s.
Good luck and wishing you well Trudy
LikeLike